Public Authentication is designed for Device-to-Server scenarios where the Verification API has to be called in untrusted environment - i.e. mobile application on end user's phone. In such case secret could be extracted from app, and used to send fraudulent traffic. This authentication methods uses additional out of process webhook to authorize API call.
When a request is received, Verification sends a Verification Request Event to a Callback URL configured in the app settings on the Dashboard. If the callback is not handled, the verification process will be rejected. It's important to correlate callbacks with your business processes to prevent fraud.
Below is a pseudocode example of setting up an Authorization header for requests to Sinch:
Authorization = "Application " + ApplicationKeyYou can configure the Callback URL in the Sinch Dashboard for each application.
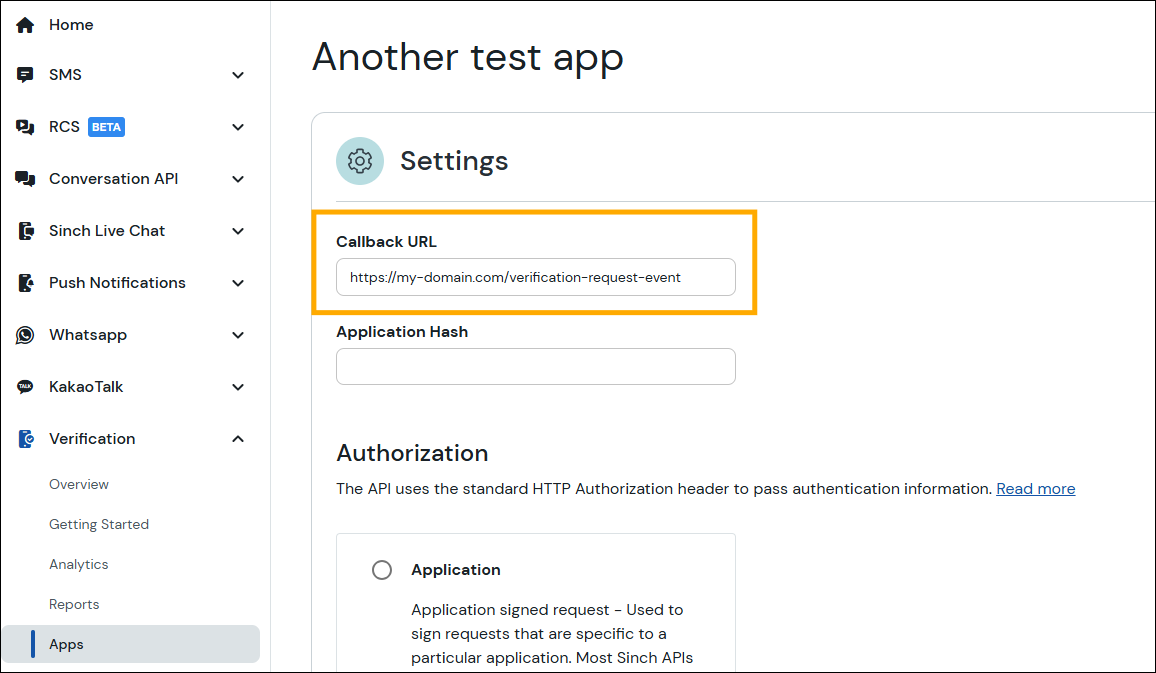
Callbacks sent to your backend are signed by Verification. See Callback Request Signing for details.
Always verify that the callback is from Sinch by checking its signature.
When your backend receives a callback, you must:
- Correlate it with your business process - do not respond "Allow" to all messages.
- Decide whether to allow or deny the verification.
Improper or careless callback setup can expose you to fraud and attacks like Artificial Inflation of Traffic (AIT). AIT generates fake traffic, increasing costs and compromising security.
For details on callback request and response schemas, refer to the Verification Callbacks section.